Important Protocols
The Information provided below is extracted from Various Internet sources and from various book I read till now such as Network Basic for hacker (by master OTW),The Tangled Web A Guide to Securing Modern Web Applications (By Michal Zalewski),etc.All credit goes to them I just extracted the info from different places and Presented it in one place by modifying them a little in my own words so that it becomes easy to understand for anyone.
Protocols in the internet world are sets of rules and conventions that govern how data is transmitted, received, and processed across computer networks. They play a fundamental role in ensuring that different devices and systems can communicate with each other effectively. Protocols are like the language that computers use to understand and interact with each other.
Sometimes when someone who is new into this field tries to search-up the internet for the information regarding protocols , the results can be extremely overwhelming for them. My only motive to create this article was to give the basic understanding of different protocols to anyone who is completely new in this field. We will discuss few basic Important Protocols ,I will keep updating this list of protocols in future!
FTP - 20,21(TCP)
- File Transfer Protocol (FTP) is, as the name suggests , a protocol used to allow remote transfer of files over a network. It uses a client-server model to do this.
- The File Transfer Protocol (FTP) is a standard network protocol used for the transfer of computer files between a client and server on a computer network.
- A typical FTP session operates using two channels:
- a command (sometimes called the control) channel
- a data channel.
- FTP operates using a client-server protocol. The client initiates a connection with the server, the server validates whatever login credentials are provided and then opens the session
- FTP runs on port
21by default , sometimes it may run on port20as well.
SSH - 22(TCP)
- SSH or Secure Shell or Secure Socket Shell, is a network protocol that gives users a secure way to access a computer over an unsecured network. Default port:
22 - SSH is an improved version of telnet , as in TELNET the data used to trasmit in cleartext but in SSH the data is encrypted.
- Sometimes you may get error while trying to login to few machines , so you can try this command to fix that
oHostKeyAlgorithms=+ssh-dss - There are different types of ssh logins ;
Host-based Authentication:
- Host-based authentication relies on the client host’s identity, and it is generally less secure and less commonly used compared to other methods.
- It authenticates users based on the client’s hostname or IP address
Public key Authentication:
- Public key authentication is a more secure method than password authentication.
- It involves generating a key pair consisting of a public key and a private key. The public key is stored on the server, and the private key is kept securely by the client.
- When the client attempts to connect, it uses its private key to prove its identity to the server. If the server has the corresponding public key, the client is granted access.
- This method is commonly used in production environments and is highly recommended for better security.
Password Authentication:
- This is the most basic form of SSH authentication, where the user provides a username and password to log in.
- While simple, it may not be the most secure method, especially if weak passwords are used.
Two-Factor Authentication (2FA):
- Two-factor authentication adds an extra layer of security to SSH login.
- In addition to the username and password or public key, users must provide a second factor, such as a one-time code generated by a mobile app or sent via SMS.
- This method helps protect against unauthorized access, even if passwords or private keys are compromised.
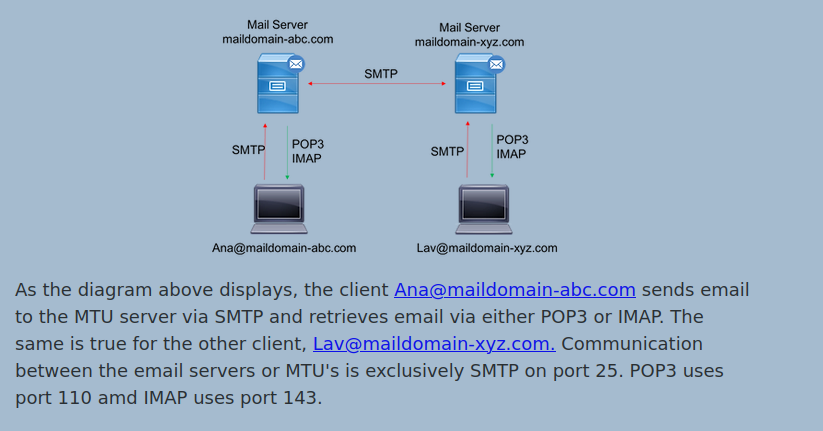
SMTP - 25,587 (TCP)
- SMTP stands for “Simple Mail Transfer Protocol”. It is utilised to handle the sending of emails. In order to support email services, a protocol pair is required, comprising of SMTP and POP/IMAP. Together they allow the user to send outgoing mail and retrieve incoming mail, respectively.
- Simple Mail Transport protocol or SMTP as it is commonly known, is among the most important protocols in our digital age.It is used to transfer email from one user to another. Although SMTP was first codified in 1983, it is still this same protocol that carries nearly all email with some enhancements.
- The SMTP server performs three basic functions:
- It verifies who is sending emails through the SMTP server.
- It sends the outgoing mail
- If the outgoing mail can’t be delivered it sends the message back to the sender
- Ports Used
25,465,587. Originally, the Simple Mail Transfer Protocol (SMTP) used port 25. Today, SMTP should instead useport 587— this is the port for encrypted email transmissions usingSMTP Secure (SMTPS) POP, or “Post Office Protocol” andIMAP, “Internet Message Access Protocol” are both email protocols who are responsible for the transfer of email between a client and a mail server.
Telnet - 23(TCP)
- Telnet is similar to ssh but its not encrypted which means that all the data it sends or receives is in plain text and it can can be read by any attacker using wireshark or anyone by interception the traffic. Telnet runs on tcp port
23by default. - Telnet is an application protocol which allows you, with the use of a telnet client, to connect to and execute commands on a remote machine that’s hosting a telnet server.
- The telnet client will establish a connection with the server. The client will then become a virtual terminal- allowing you to interact with the remote host.
- Telnet sends all messages in clear text and has no specific security mechanisms. Thus, in many applications and services, Telnet has been replaced by SSH in most implementations.
How Does Telnet Work?
The user connects to the server by using the Telnet protocol, which means entering “telnet” into a command prompt. The user then executes commands on the server by using specific Telnet commands in the Telnet prompt. You can connect to a telnet server with the following syntax:
telnet [IP] [PORT]
DNS - 53(UDP/TCP)
- The Domain Name System or DNS is one of those network protocols that makes the world go round. Without it, we would need to remember innumerable IP addresses just to navigate to our favorite web sites. Imagine trying to remember the IPv4 (32-bit) addresses of Facebook, Amazon and Hackers-Arise, just to visit each of those critically important web sites (only made worse by IPv6 128-bit addresses). DNS runs on port
53by default. - DNS was designed to translate a domain name–something people are rather good at remembering–into an IP address, the language of Internet Routing. Think of DNS as simply a translation of a domain name to their respective IP addresses. So, when you enter a domain such as www.google.com into your browser, it is translated into a computer-friendly IP address (172.217.167.174) that the Internet can understand and route.
- DNS uses
TCPfor zone transfer andUDPfor name queries either regular or reverse. - IN DNS ,
UDPcan be used to exchange small information whereasTCPmust be used to exchange information larger than512 bytes.
Domain Names
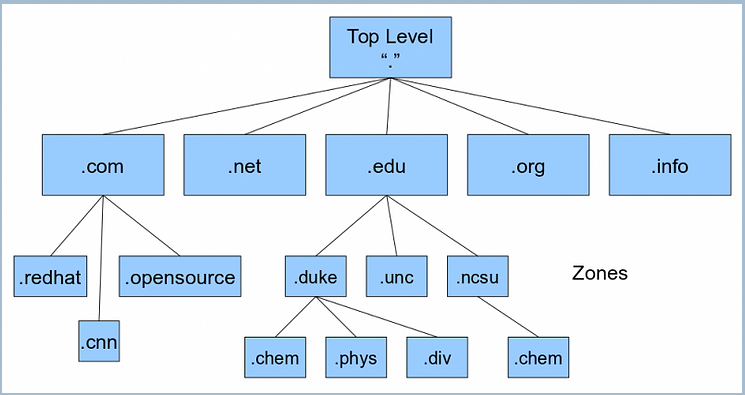
Domain names must be registered with ICANN (Internet Corporation for Assigned Names and Numbers) usually through an intermediary such as VeriSign or GoDaddy. Top Level Domains or TLD’s include
.com, .edu, .organd many others that we typically seen at the end of Full Qualified Domain Name (FQDN).- DNS works in a hierarchical manner. The Top Level Domains or TLD’s can have multiple sub domains under them. In the diagram above, both .redhat and .cnn are part of the Top Level Domain .com. A sub domain is a domain that is part of larger domain. In this example, redhat and cnn are often just referred to as the domain in common parlance, but are actually the Second Level Domain or (SLD) under .com.
- Then, beneath these SLD’s or commonly referred to domains, we many subdomains. For instance, within and beneath .redhat, we might have sales.redhat, engineering.radhat, development.redhat. This is a method of subdividing the domain. The left most portion is always the most specific, while the right most is most general.
How DNS Works?
- Now that the Internet contains billions of IP addresses and FQDN, the host file is woefully inadequate. Enter DNS. First developed by Paul Mockapetris (now in the Internet Hall of Fame) in 1983, DNS is both distributed and dynamic, unlike our hosts file.
- DNS does not rely upon one file or one server, but instead upon many files across many server across the globe. These servers are organized in a hierarchical manner. Due to this distributed nature, the DNS system is resistant to outages of one or many of these servers.
DNS Components
- The DNS service has four (4) components;
- DNS Cache
- Resolvers
- Name servers
- Name space
DNS cache
This term is often confused as it has at least two meanings. First, DNS cache can be the list of names and IP addresses that you have already queried and have been resolved and are cached for you so that no network traffic is generated to resolve them (and much quicker). The second meaning regards a DNS server that simply performs recursive queries and caching without actually being an authoritative server itself.
Resolvers Resolvers are any hosts on the Internet that need to look up domain information, such as the computer you are using to read this website. ( Converting Domain Names into IP Address)
Name servers= These are servers that contain the database of names and IP addresses and serves DNS requests for clients.
Name space Name space is the database of IP addresses and their associated names.
Zone Files and Records
- Every DNS zone has a zone file. This zone file may be thought of as DNS database. These zone files have one or more resource records. These DNS records must be periodically be updated as new domains are added, changed and others dropped. Without this process, the system would remain stagnant and eventually be completely out of date. Therefore, it is essential that DNS server be capable of zone transfers.
Common Resource record types -
SOA record
- The Start of Authority, or SOA, record is a mandatory record in all zone files. It must be the first real record in a file (although $ORIGIN or $TTL specifications may appear above). It is also one of the most complex to understand. The fields includes the primary name server, the email of the administrator, the domain number and timers for refreshing the zone
NS Records
- NS or name server identifies the authoritative DNS server for the zone
A Records
- The A (Address) record is used to map a domain or subdomain to an IPv4 address. For instance, hackers-arise.com points to 23.236.62147.
AAAA Records
- AAAA records point to an IPv6 record.
CNAME (Canonical) records
- The CName or canonical name maps one domain or subdomain to another domain name.
PTR Records
- PTR Records are used in reverse DNS records (i.e. from IP address to hostname). PTR or Pointer points to a canonical name and just the name is returned in the query. You might think of these as the reverse of A or AAAA records.
MX Records
- The MX record directs mail to a specific a mail server responsible for accepting of mail in the zone. Like CNAME, the MX record must always point to a domain and never an IP address.
DNS Security or DNSSec
- DNS by default is NOT secure. DNS can be easily spoofed due to the fact that DNS is based on UDP, which is not connection-oriented. DNSSEC or DNS Security Extensions was developed to strengthen the authentication in DNS by using digital signatures.
Every DNS zone has a public/private key. Any recursive resolver that looks up data in the zone, also retrieves the zone’s public key which can used to validate the authenticity of the data.
Before DNSSec, it was possible for malicious actors to execute zone transfers on DNS servers. This would poison the data making it unreliable. DNSSEC prevents this by;
- Cryptographically verifying that the data it receives actually comes from the zone it believes it should come from;
- Insuring the integrity of the data so that the data can’t be altered enroute as the data must be digitally signed by the private key of the zone.
SMB - 445(TCP) | Netbios - 137(UDP/TCP),138(UDP),139(TCP)
NetBIOS (Network Basic Input Output System)
It provides services related to the session layer of the OSI model allowing applications on separate computers to communicate over a local area network. As strictly an API, NetBIOS is not a networking protocol. In modern networks, NetBIOS normally runs over TCP/IP via the NetBIOS over TCP/IP (NBT) protocol. This results in each computer in the network having both an IP address and a NetBIOS name corresponding to a (possibly different) host name.
- NetBIOS provides name servicing, connectionless communication and some Session layer stuff
- The browser service in Windows designed to host information about all machines within domain or TCP/IP network segment
- NetBIOS name is a 16-character ASCII string used to identify devices
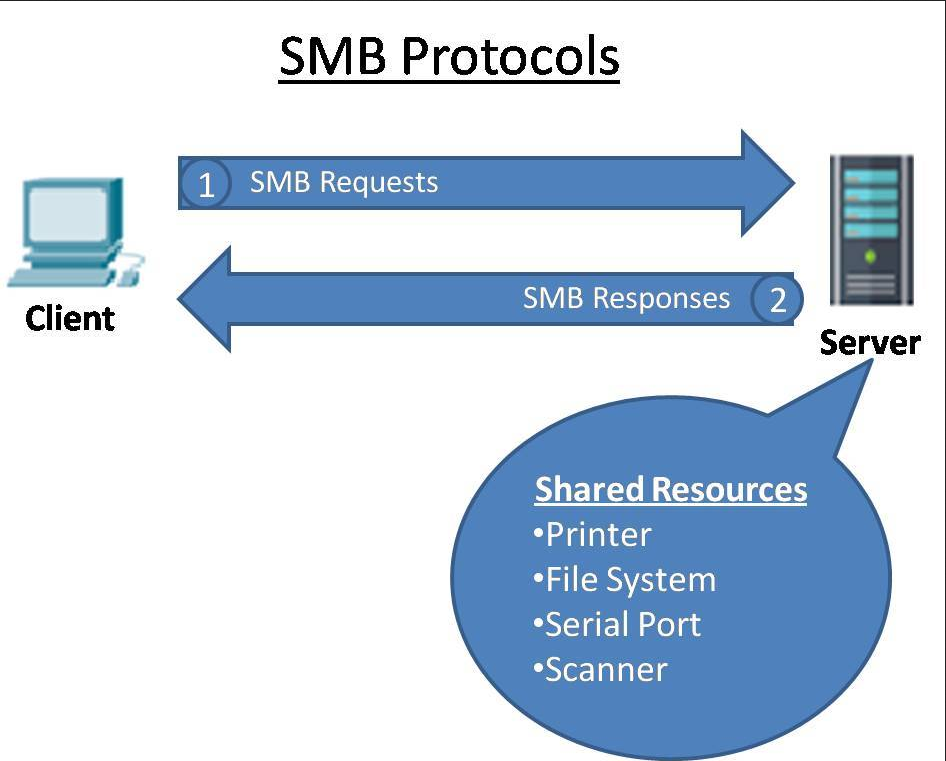
SMB (Server Message Block)
Server Message Block, the modern dialect of which is known as Common Internet File System, operates as an application-layer network protocolmainly used for providing shared access to files, printers, serial ports, and miscellaneous communications between nodes on a network.
What is the relationship between SMB and NetBIOS; are they separate, does one rely upon the other?
- SMB does rely on NetBIOS for communication with devices that do not support direct hosting of SMB over TCP/IP.
- NetBIOS is completely independent from SMB. It is an API that SMB, and other technologies can use, so NetBIOS has no dependency to SMB.
The Server Message Block protocol can run on top of the Session (and lower) network layers in several ways:
- Directly over TCP, port
445 microsoft-ds if windows or SAMBA if Linux - On Windows, SMB can run directly over TCP/IP without the need for NetBIOS over TCP/IP. This will use, as you point out, port
445 - via the NetBIOS API, which in turn can run on several transports: on
UDP ports 137, 138 & TCP ports 137, 139 – see NetBIOS over TCP/IP
Generally speaking, on other systems, you’ll find services and applications using port 139. This, basically means that SMB is running with NetBIOS over TCP/IP, where, stack-wise, SMB is on top of NetBIOS if you have to imagine it with the OSI model.
Check the properties of your network card. Somewhere in the Advanced IP Settings is a checkbox “Enable NetBIOS over TCP”. Activate it and your computer uses port 139. Deactivate the option and the system wants to use 445.
Port 139: SMB -> NetBIOS -> TCPPort 445: SMB -> …. -> TCP
As you can see, the relationship would be Application -> SMB -> NetBIOS -> (TCP/IP, others).
SNMP - 161(UDP)
The Simple Network Management Protocol or SNMP is among the least understood protocols, yet so vitally important to the successful operation of your network.If an attacker can breach the SNMP, they may be able to unmask your encrypted VPN communication, as well as see and possible control every device connected to your network.
The Simple Network Management Protocol uses UDP ports 161 and 162 to manage network devices. When used with Transport Layer Security or Datagram Transport Layer Security, requests are received on port 10161 and notifications are sent to port 10162. Network devices use this protocol to communicate to each other and can be used by administrators to manage the devices. As hackers, if we can access the SNMP protocol, we can harvest a vast resource of information on the target’s network and even disable and change the settings on these devices. Imagine the havoc one could wreak by changing the settings on routers and switches!
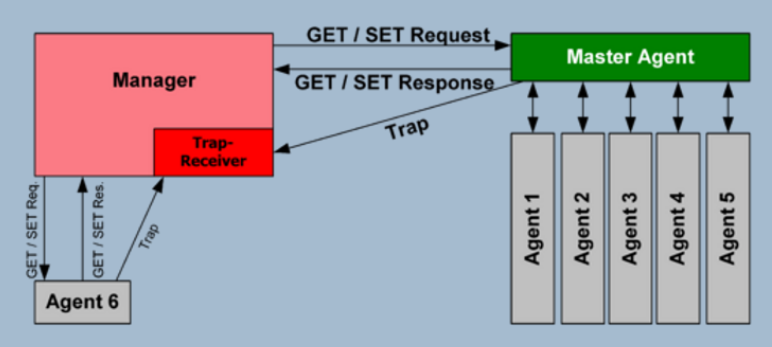
SNMP is a stateless, datagram oriented protocol. It involves one or more administrative computers called managers. These managers monitor and manage a group of computers. Each of the managed computers has an agent installed that communicates with the manager. Please see the diagram below for a schematic on how SNMP operates.
The agent on the managed computers provides management data to the managing computer. The manager can undertake management tasks, including modifying and applying new configurations.
The management data exposed by the agents on each of the managed machines is stored in a hierarchical database called the Management Information Bases or MIB. It is this information within the MIB that we will be seeking here. This MIB contains a vast array of information on every device on the network, including users, software installed, operating systems, open ports, etc. All of this information can be invaluable in developing an exploitation strategy on the target.
SNMP has three (3) versions. Version 1 or SNMPv1, has very poor security. The authentication of clients is in cleartext and by default, uses a "community string" that is set to "public". This community string operates like a password and it is valid for each and every node on the network. The authentication of the manager is also a community string set to "private",by default. With these community strings, the attacker can gather all the information from the MIB (with the public community string) and even, set the configuration on the devices (with the private community string). Although it is widely known and understood that SNMPv1 is insecure, it remains in wide use.Even if the network administrator changes the community string from the defaults, because communication is in cleartext, an attacker can sniff the authentication strings off the wire.
SNMPv2 improved upon SNMPv1 in terms of performance and security, but because it was not backwardly compatible with SNMPv1, it was not widely adopted. SNMPv3 is significantly more secure than either SNMPv1 or v2. SNMPv3 adds encryption, message integrity and authentication, but is still not used on all networks.
NFS - 2049(TCP)
NFS stands for Network File System and allows a system to share directories and files with others over a network. By using NFS, users and programs can access files on remote systems almost as if they were local files. It does this by mounting all, or a portion of a file system on a server. The portion of the file system that is mounted can be accessed by clients with whatever privileges are assigned to each file.
If someone wants to access a file using NFS, an RPC call is placed to NFSD (the NFS daemon) on the server.
HTTP - 80(TCP) | HTTPS - 443(TCP)
The HyperText Transfer Protocol, or HTTP, is the granddaddy of web technologies. It is the core communication protocol of the web, and all web applications use it. It’s a simple protocol originally designed to retrieve static web pages. Over the years, it has been updated and extended to offer support to complex applications that are common today.
HTTP uses a message-based model where the client sends a request, and the server responds with a response. It is connection-less but uses TCP as its transport mechanism.
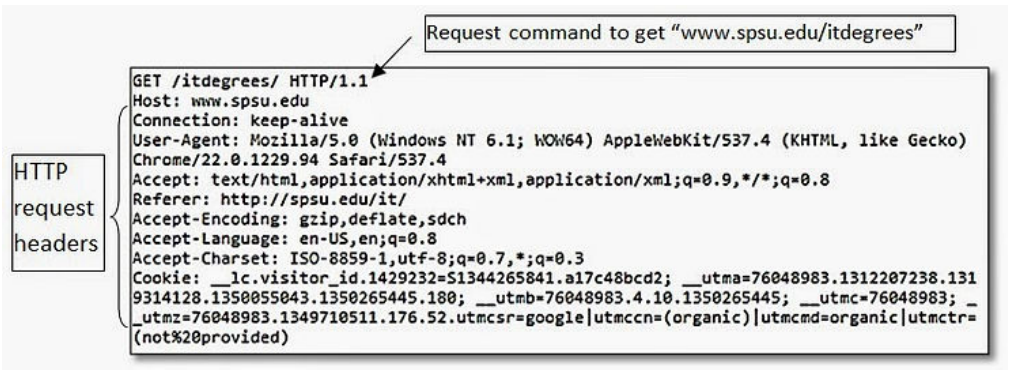
HTTP Requests
All HTTP messages contain the same basic elements;
- One or more headers
- Then a blank line
- An optional Message Body
The first line of the HTTP requests has three elements, separated by spaces
- A verb (action word) indicating the HTTP method (see methods below). Among these, the most common is GET. The GET method retrieves a resource from the web server
- The requested URL
- The HTTP version used
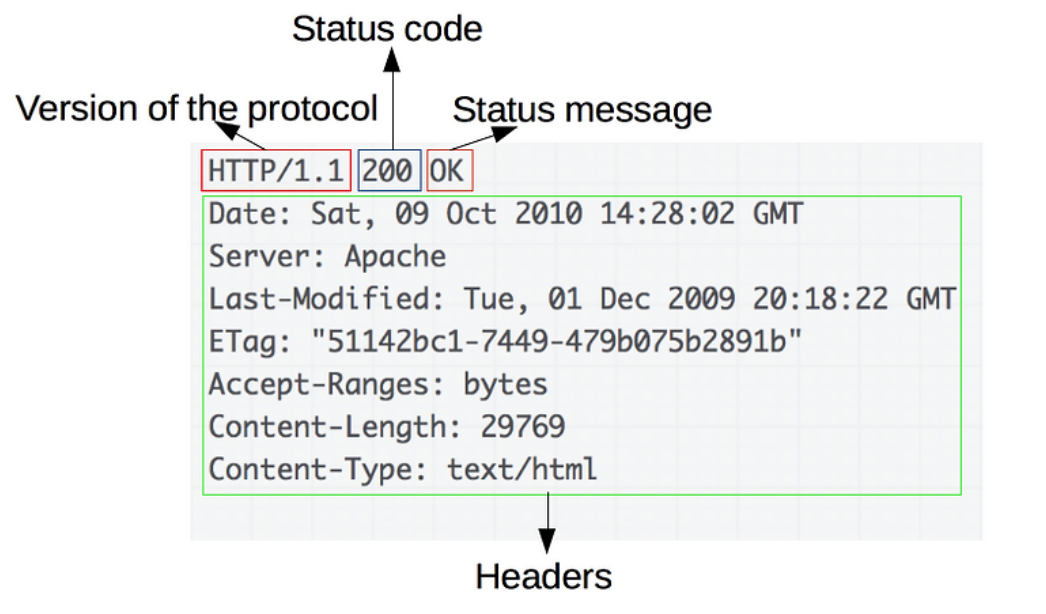
HTTP Responses
The typical HTTP response consists of three items;
- The HTTP version
- The numeric status code (see status codes below).
- The text describing the status response.
HTTP Methods
When we attack web applications, we are most commonly making a request to the web server. This means that our methods will likely be either a POST or GET. There are subtle differences between these two requests.
- The
GETmethod is built to retrieve resources. - The
POSTmethod is built to perform actions. - The
HEADfunctions similarly to aGETrequest, but no message body is returned - The
TRACEis used for diagnostic purposes - The
OPTIONSasks the server to report HTTP methods are available - The
PUTattempts to upload a resource to the server, which is contained in the body
URL’s
The uniform resource locator (URL) is a unique ID for every web resource for which a resource can be retrieved. This is the all-familiar URL that we use every day to access information on the web.
The basic syntax of the URL is:
protocol://hostname[:port]/ [/path/] file [?param=value]
The port number is optional and only necessary if the port is different from the default port used by the protocol specified in the first field (http=80, https=443, ftp=21, etc.).
HTTP Headers
There are numerous types of HEADERS in HTTP. Some can be used for both requests and responses, and others are specific to the message types. These are some of the common header types;
General Headers
Connection- tells the other end whether the connection should closed after HTTP transmissionContent-Encoding- specifies the type of encodingContent-Length- specifies the content lengthContent-Type- specifies the content typeTransfer-Encoding- specifies the encoding on the message body
Request Headers
Accept- specifies to the server what type of content it will acceptAccept-Encoding- specifies to the server what type of message encoding it will acceptAuthorization- submits credentialsCookie- submits cookies to the serverHost- specifies the host nameIf-Modified-Since- specifies WHEN the browser last received the resource. If not modified,the server instructs the client to use the cached copyIf-None-Match- specifies entity tagOrigin- specifies the domain where the request originatedReferrer- specifies the URL of the requestorUser-Agent- specifies the browser that generated the request
Response Headers
Access-Control-Allow-Origin- specifies whether the resource can be retrieved via cross-domainCache-Control- passes caching directive to the browseEtag- specifies an entity tag (notifies the server of the version in the cache)Expires- specifies how long the contents of the message body are validLocation- used in redirect responses (3xx)Pragma- passes caching directives to the browserServer- specifies the web server softwareSet-Cookie- issues cookiesWWW-Authenticate- provides details of the type of authentication supportedX-Frame-Options- whether and how the response may be loaded within the browser frame
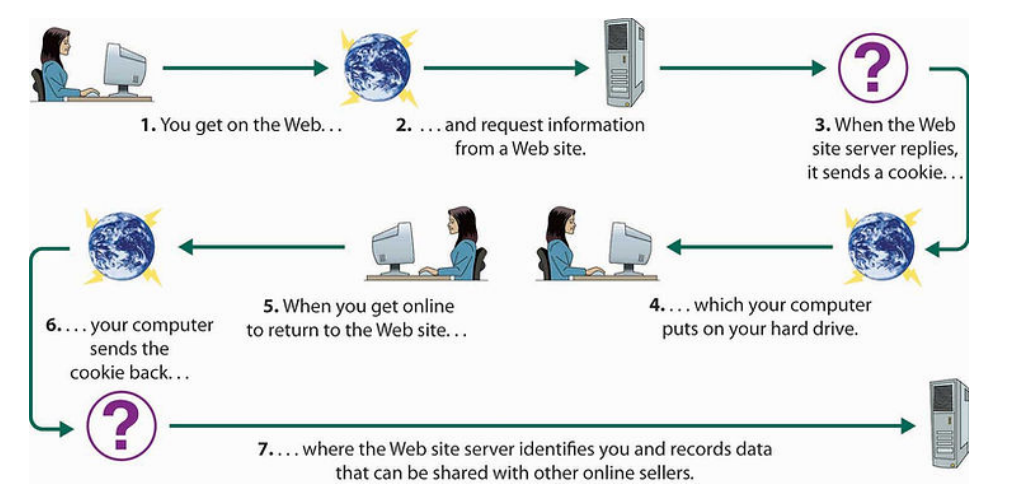
Cookies
Cookies are a critical part of HTTP. Cookies enable the server to send items of data to the client, and the client stores this data and resubmits it to the server the next time a request is made to the server.
The server issues a cookie to the client using the SET-COOKIE response header.
SetCookie: Tracking=wdr66gyU34pli89
When the user makes a subsequent request to the server, the cookie is added to the header.
Cookies are used to identify the user of the server and other key information about the server. These cookies are usually a name/value pair and do not contain a space.
Status Codes
Every HTTP response must contain a status code indicating the result of the request. There are five groups of status codes based on the first digit of the code
1xx- Informational2xx- Success3xx- Redirect4xx- Error5xx- The server encountered an error
The status codes you are most likely to encounter are;
100- Continue200- OK201- Created301- Moved Permanently302- Found304- Not Modified400- Bad Request401- Unauthorized403- Forbidden404- Not Found405- Method Not Allowed413- Request Entity Too Large414- Request URI Too Long500- Internal Server Error503- Service Unavailable
HTTPS
- The HTTP protocol is transmitted in plain TCP, which means it is unencrypted and susceptible to MitM attacks and other such attacks by an attacker positioned between the client and server.
HTTPSis essentially the same as HTTP but instead is tunneled usingSecure Sockets Layer(SSL).- In this way, the confidentiality and integrity of the data are protected.
HTTP Authentication
The HTTP protocol has its own mechanisms for authenticating users. These include;
Basic: sends user credentials as Base64-encoded string in the request header
NTLM: challenge-response mechanism
Digest: challenge-response and uses MD5 checksums of a nonce with user’s credentials.